

All the answers to your questions can be found in our frequently asked questions. If you can not find the answer to your question on this webpage, you can contact us.
The CRDF Threat Center is a service published by the independent French laboratory CRDF Labs. This service detects malicious URLs that violate our detection criteria and integrates these URLs into our databases to combat cybercrime.
CRDF Labs develops its own detection systems, sharing with others our threat intelligence data and technologies to fight and detect security risks. CRDF Labs is a nonprofit laboratory, independent and completely transparent to its users.
The CRDF Labs laboratory has its own R & D and its own detection and analysis tools. The CRDF Threat Center is a demonstration of our unique know-how in the detection of security risks on the Internet.
These technologies are based on our old Blockulicious, Blockulicious DNS and CRDF Sandbox products.
We do not want anyone to be infected with this homepage accessible to everyone. We prefer someone interested in our databases to come forward and contact us to discuss possible access to CRDF Threat Center's private area.
No. The CRDF Threat Center is a non-commercial project and our internal technologies are not for sale.
If you wish to use our services or our database, you must comply with this license and our terms of use (ToS).
If your website is contained in our database, our systems have found a violation of our detection criteria. Thank you for complying with it to be removed from our database and make a false positive statement. CRDF Labs never indicates exactly why a URL is embedded in our database.
No, sorry. CRDF Labs never gives more information about a website considered contrary to our detection criteria. CRDF Labs is not intended to provide any evidence that a website is against our detection criteria. The purpose of CRDF Labs is to protect its users against security risks associated with a browser over the Internet.
You should understand that CRDF Labs is a non-commercial and voluntary project. As such, we do not wish to respond to these requests for reasons of efficiency. Indeed, it would be impossible for our services to give a personalised answer to all the people who contact us.
If you contact us for a specific reason, you will not receive a reply from us. Please take this into consideration before contacting us.
If our system tells you that the URL is not contained in our database, your website is not contained in our database and your website is not blacklisted. No need to contact us to ask for information, we would have nothing more to communicate to you.
This is perfectly normal. The propagation can take several hours to get synchronized with VirusTotal. It is not necessary to contact us to report this error. Everything is automatic and the process will automatically delete the detection on VirusTotal at the next occurrence.
If you still have it after hours, consider refreshing the report when scanning a VirusTotal URL.
To update the report on VirusTotal, please click on this icon:
No. We no longer have any products that allow us to block malicious sites in our database. Only users / companies using our database will block websites that we report as not meeting our detection criteria.
We are French and we are based in Paris. We are not a company but an independent laboratory and without any legal status.
Yes it is possible as long as you respect our license of use, that you use it non-commercial and that you share threat intelligence data with us.
* Phishing:URL : this web address is recognized by our engines as a phishing address
* Malware:URL : this address is recognized by our engines as an address distributing malware (exe, dll, dmg, etc.)
* Malicious:URL : this address is recognized by our engines as an address being in disharmony with our detection criteria
* Suspect:URL : this address is recognized by our engines as a suspicious address and is probably an infection source / does not meet our detection criteria
Yes, we have an automatic system that ensures the overall consistency of the database. A website that meets our new detection criteria will be automatically removed from the database after a certain period of time. This time is random and we can not guarantee that your Site will be deleted. Please refer to the false positive statement.
WARNING: this procedure does not allow you to have CRDF Labs remove your website from our databases. This PROCEDURE ONLY allows you to request that your domain name be added to our system so that it is never added again. If you wish to report a false positive and have your website removed from our database, please go to the appropriate procedure accessible from the CRDF Threat Center.
CRDF Labs integrates in its analysis systems a white list allowing it to consider domain names as safe and which will be automatically ignored by our engines.
We can only whitelist one or more domain names. We cannot recognize a specific marker other than a domain name and/or IP address.
If you want to be added to our whitelist, you must meet the following conditions:
- be a site with a large audience and/or recognized in your field of activity
- demonstrate that your activity does not violate our detection criteria (if you have been added to our database, there is a reason)
- have completed three (*3*) false positive requests through our removal process
If you meet these criteria, you can contact us and request to be added to our whitelist. Don't forget to demonstrate that your activity is legitimate according to our detection criteria.
CRDF Labs is under no obligation to provide evidence of non-compliance with our detection criteria. The service is provided as is without warranty and is non-commercial. CRDF Labs is completely independent and when we add a site to our database, it is not blocked anywhere and it can not be harmful such as antivirus or blockages from Google SafeBrowing for example. We will provide evidence in specific cases and within a legal framework governed by French law.
If you have not received a response to your email, you should not have followed the procedure indicated to declare a false positive, declare an error in the treatment of your false positive or you did not follow a specific procedure. These procedures allow us to deal with the many requests that we constantly receive.
Please follow the procedure and contact us if you have a problem with this procedure.
For our static analyzes, we use the following engines:
- Avast (thank you very much to them, we like this engine very much)
- Dr.Web
- ClamAV
- Ikarus (thank you very much to them)
The Avast and Ikarus engine is provided to us free of charge as part of a partnership between the publisher and CRDF Labs. Thank you very much to them for their trust.
We cannot clearly tell you our output IP addresses from our scanning tools for security reasons. Indeed, malicious individuals could block our IP addresses to prevent us from scanning their infrastructures.
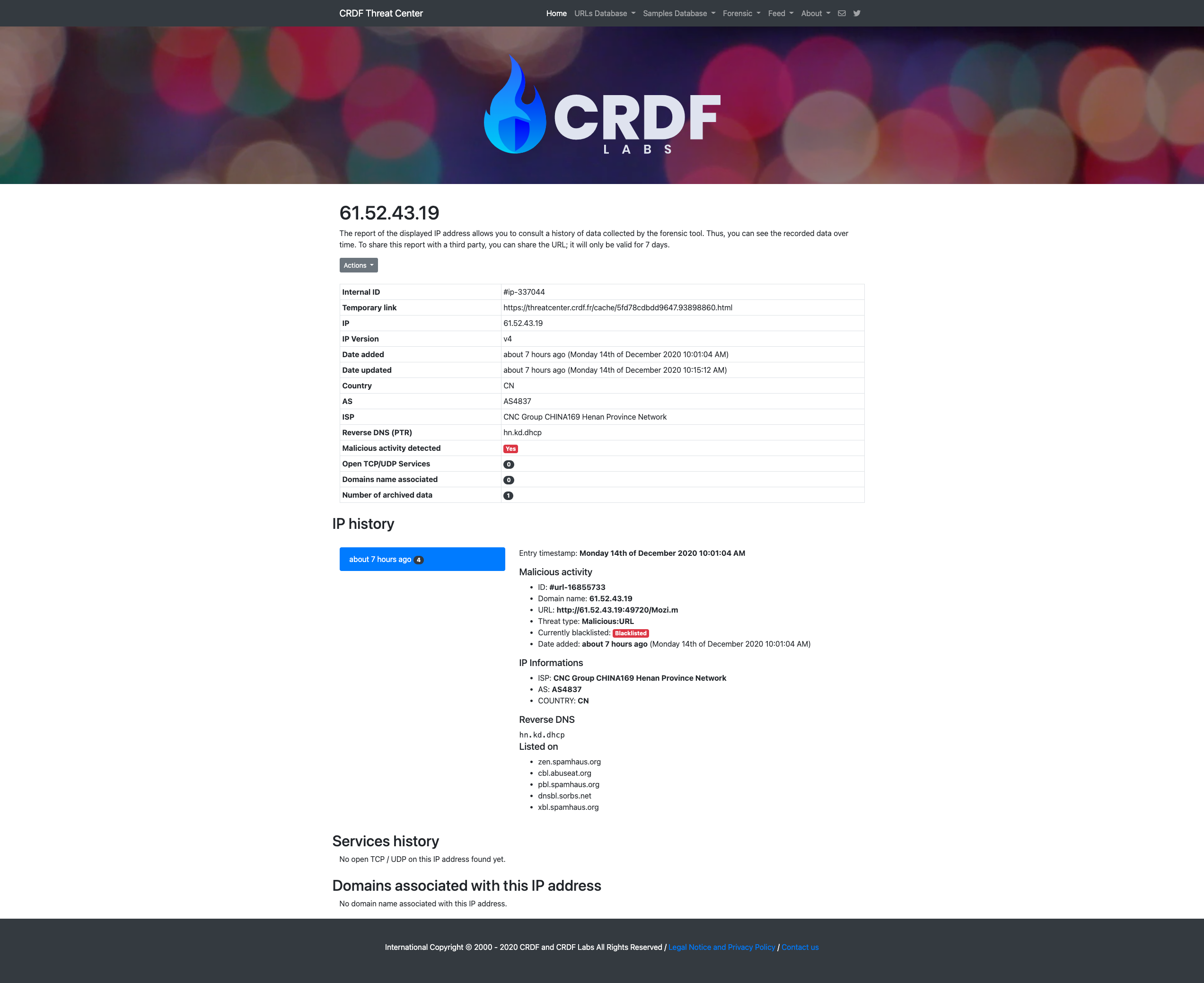
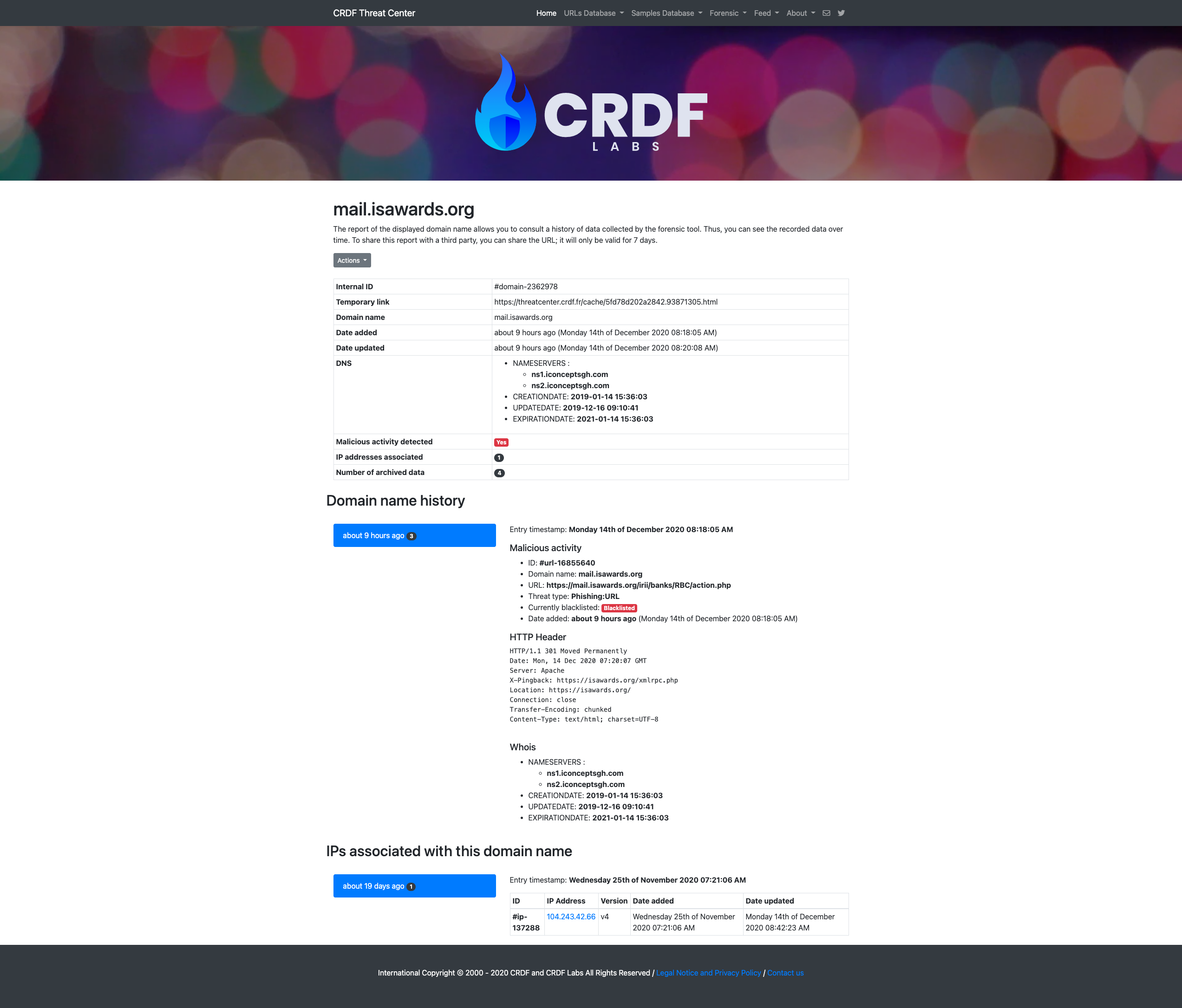
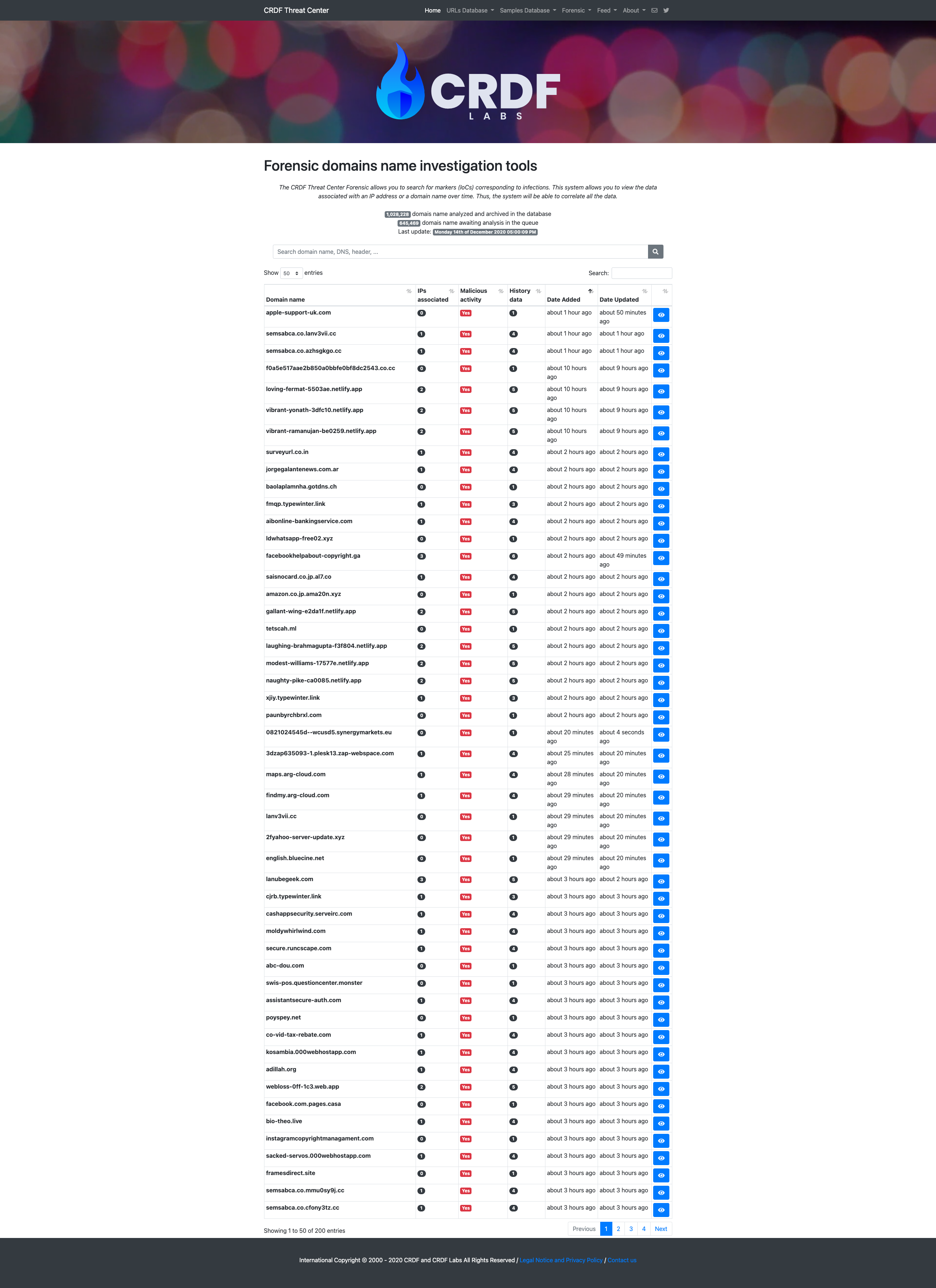
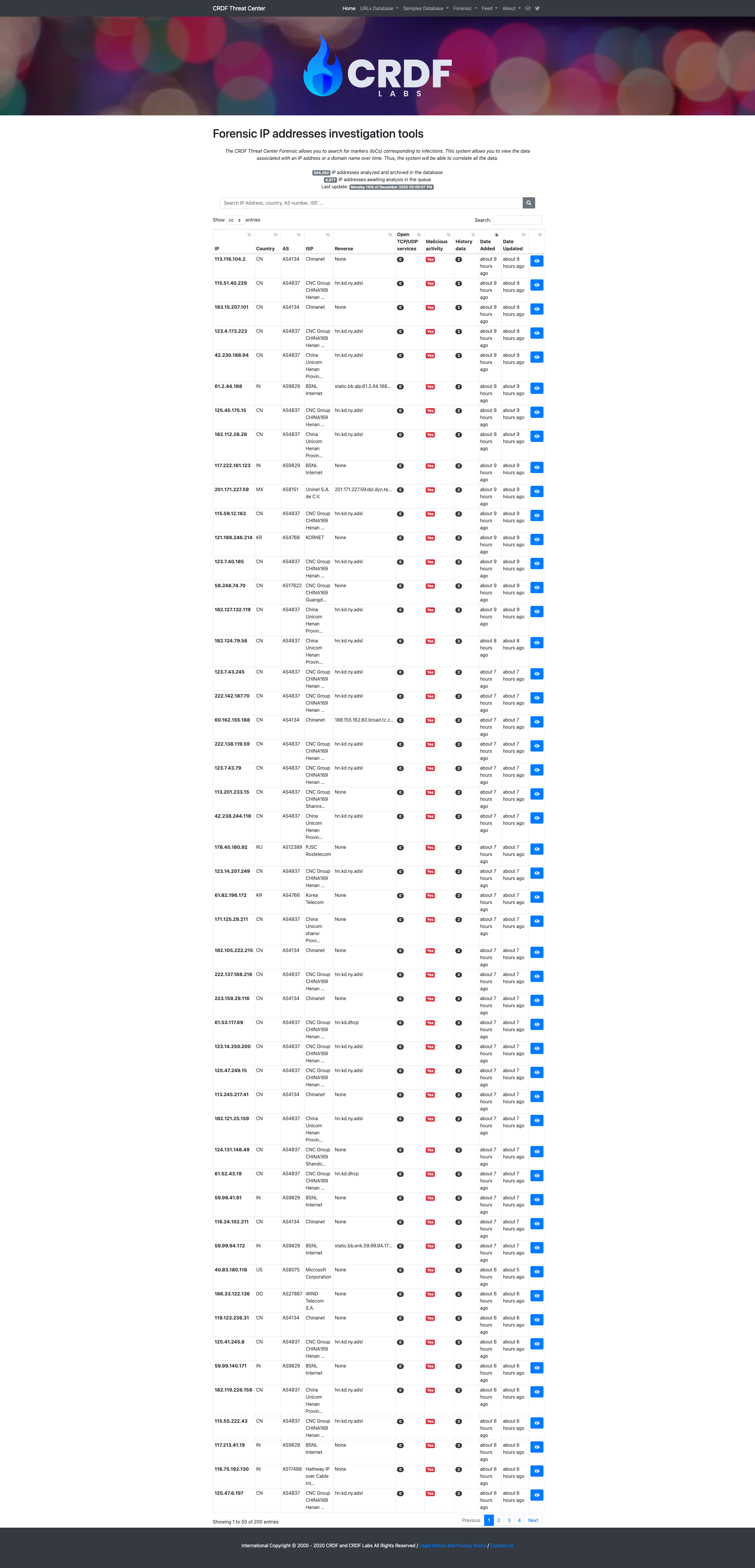
The CRDF Threat Center Forensic allows you to search for markers (IoCs) corresponding to infections. This system allows you to view the data associated with an IP address or a domain name over time. Thus, the system will be able to correlate all the data.
It allows you to search for the following indicators:
- domain names
- ip addresses
Each marker is analyzed several times by our system and it is able to give you an overview over time of a given marker.
The data that we save (not exhaustive):
- associated IP addresses
- Headers
- NS
- MX
- Open TCP / UDP ports
- Reverse DNS
- DNSBL
- Malicious activity
- Evolution of the marker
- IP and related domain names
A search engine allows you to search our databases for specific markers and also in data (IP addresses, specific threats, etc.).
Some screenshots of the service:
To stop these alerts, you can click on this link indicated in our emails which will allow you to block all future alerts.
If you host products shared via the same IP address (VPN, Various services, Proxy, etc.), it is your responsibility to secure these accesses. CRDF Labs does not detect illegal activity for nothing. We will also not be able to delete you from our databases.
This argument is totally false. We cannot impact your business with our detection because we are not blocking anything.
Like antiviral products, their customers cannot access detected malicious websites. With us, we do not carry out any blocking. It is simply a directory.
This argument is therefore totally false. Your business may not be impacted by our services.
To increase the limitations imposed by your API key, you must contact us with a precise description of your needs.
After study, we will come back to you to give you our decision.
After a false positive request via our form, you may be contacted by our experts to ask you for information and to clarify certain things.
This is the email you should have received:
Hello,
False Positive Reference #XXXXXXXXXXXXXXX
At your request, CRDF Labs conducted a new analysis of the domain name "domain.com".
We regret to inform you that we can not delete your domain name to our database since it corresponds to a malicious website (in confirmation with our criteria for detection and characterization of malicious websites).
Thank you kindly refer to the following page in our Knowledge Base to know our detection criteria: https://threatcenter.crdf.fr/criteria.html.
Thank you kindly note that we take very seriously the claims of false positives and we take all measures to respond favorably to your request.
///////
WARNING
///////
PLEASE READ CAREFULLY THE INFORMATION CONTAINED BELOW. THIS INFORMATION WILL LET YOU KNOW THAT YOU DO NOT AGREE WITH OUR DECISION.
PLEASE DO NOT CONTACT US WITHOUT FOLLOWING THIS PROCEDURE.
*** Important notes ***: CRDF Labs never gives more information about a website considered contrary to our detection criteria. CRDF Labs is not intended to provide any evidence that a website is against our detection criteria. The purpose of CRDF Labs is to protect its users against security risks associated with a browser over the Internet. So, you have to understand we cannot give you more details on adding a domain name in our database.
----
If you do not agree with this decision, please follow these few steps:
1/ A report containing additional data on your application is available at the following address:
https://threatcenter.crdf.fr/false_positive.php?ref=XXXXXXXXXXXXXXX
2/ If you want to report an error from our expert during the analysis of the website, please click on the following URL:
https://threatcenter.crdf.fr/false_positive.php?ref=XXXXXXXXXXXXXXX&recall
(By clicking on this URL, an expert will analyze the website again, please do not contact us if you do not click on this link)
WARNING: If you wish to report an error in the processing of your request, please report it to us by the above procedure (by following this link: https://threatcenter.crdf.fr/false_positive.php?ref=XXXXXXXXXXXXXXX&recall). We will not respond to your request if you do not follow the procedure.
----
The background check is an internal investigation carried out by the CRDF Labs manager to determine whether you can access our data based on the information you have provided.
As you can imagine, the data contained in CRDF Labs is sensitive and we do not want malicious people to have access to it.
This brackground check allows us to verify and limit this risk by making it more difficult to interfere.
During our investigation phase, CRDF Labs may ask you by email for documents or any other information enabling us to understand the origin of your organization or for administrative documents enabling us to verify the veracity of your statements.
The Traffic Light Protocol (TLP) was created in order to facilitate greater sharing of information. TLP is a set of designations used to ensure that sensitive information is shared with the appropriate audience. It employs four colors to indicate expected sharing boundaries to be applied by the recipient(s). TLP only has four colors; any designations not listed in this standard are not considered valid by FIRST.
TLP provides a simple and intuitive schema for indicating when and how sensitive information can be shared, facilitating more frequent and effective collaboration. TLP is not a “control marking” or classification scheme. TLP was not designed to handle licensing terms, handling and encryption rules, and restrictions on action or instrumentation of information. TLP labels and their definitions are not intended to have any effect on freedom of information or “sunshine” laws in any jurisdiction.
TLP is optimized for ease of adoption, human readability and person-to-person sharing; it may be used in automated sharing exchanges, but is not optimized for that use.
TLP is distinct from the Chatham House Rule (when a meeting, or part thereof, is held under the Chatham House Rule, participants are free to use the information received, but neither the identity nor the affiliation of the speaker(s), nor that of any other participant, may be revealed.), but may be used in conjunction if it is deemed appropriate by participants in an information exchange.
The source is responsible for ensuring that recipients of TLP information understand and can follow TLP sharing guidance.
If a recipient needs to share the information more widely than indicated by the original TLP designation, they must obtain explicit permission from the original source.
Community: Under TLP, a community is a group who share common goals, practices, and informal trust relationships. A community can be as broad as all cybersecurity practitioners in a country (or in a sector or region).
Organization: Under TLP, an organization is a group who share a common affiliation by formal membership and are bound by common policies set by the organization. An organization can be as broad as all members of an information sharing organization, but rarely broader.
Clients: Under TLP, clients are those people or entities that receive cybersecurity services from an organization. Clients are by default included in TLP:AMBER so that the recipients may share information further downstream in order for clients to take action to protect themselves. For teams with national responsibility this definition includes stakeholders and constituents.
a. TLP:RED = For the eyes and ears of individual recipients only, no further disclosure. Sources may use TLP:RED when information cannot be effectively acted upon without significant risk for the privacy, reputation, or operations of the organizations involved. Recipients may therefore not share TLP:RED information with anyone else. In the context of a meeting, for example, TLP:RED information is limited to those present at the meeting.
b. TLP:AMBER = Limited disclosure, recipients can only spread this on a need-to-know basis within their organization and its clients. Note that TLP:AMBER+STRICT restricts sharing to the organization only. Sources may use TLP:AMBER when information requires support to be effectively acted upon, yet carries risk to privacy, reputation, or operations if shared outside of the organizations involved. Recipients may share TLP:AMBER information with members of their own organization and its clients, but only on a need-to-know basis to protect their organization and its clients and prevent further harm. Note: if the source wants to restrict sharing to the organization only, they must specify TLP:AMBER+STRICT.
c. TLP:GREEN = Limited disclosure, recipients can spread this within their community. Sources may use TLP:GREEN when information is useful to increase awareness within their wider community. Recipients may share TLP:GREEN information with peers and partner organizations within their community, but not via publicly accessible channels. TLP:GREEN information may not be shared outside of the community. Note: when “community” is not defined, assume the cybersecurity/defense community.
d. TLP:CLEAR = Recipients can spread this to the world, there is no limit on disclosure. Sources may use TLP:CLEAR when information carries minimal or no foreseeable risk of misuse, in accordance with applicable rules and procedures for public release. Subject to standard copyright rules, TLP:CLEAR information may be shared without restriction.
CRDF Labs does not communicate with journalists or the media. We will systematically refuse any request from an entity related to this environment.
If you believe your Website is misclassified in our database, you should follow the procedure for notifying us that we have made an error. There is no need to contact us to do this. You can access the URL "https://threatcenter.crdf.fr/false_positive.html" to report a false positive.
Fill in the form with your information. Please let us know why we made a mistake.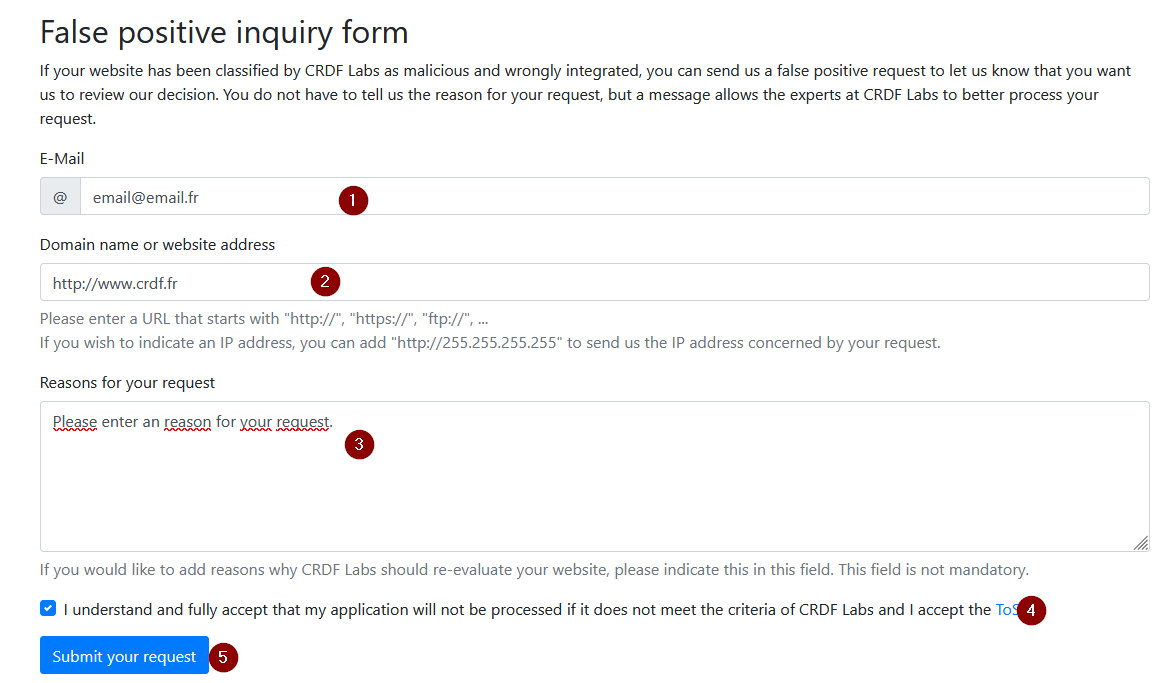
If your domain name is not in our list, you will see the following alert: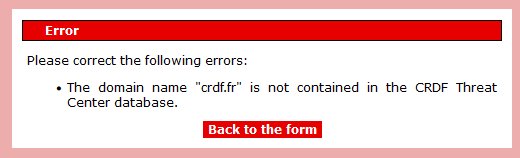
Your Website is not contained in our database. We invite you to check your entry and verify the domain name.
If your request is accepted by the system, you will get the following message with a request number: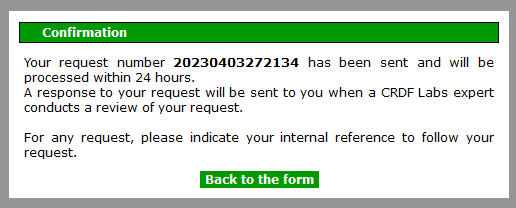
Note: remember to keep this reference number for any future requests.
From now on, your website is being analyzed by our team of experts. This analysis can take up to 24 hours. You will receive an answer directly on the email address indicated in the procedure.
Your website does not meet our detection criteria:
If the in-depth analysis of your website shows that it does not meet our detection criteria, you will receive this email: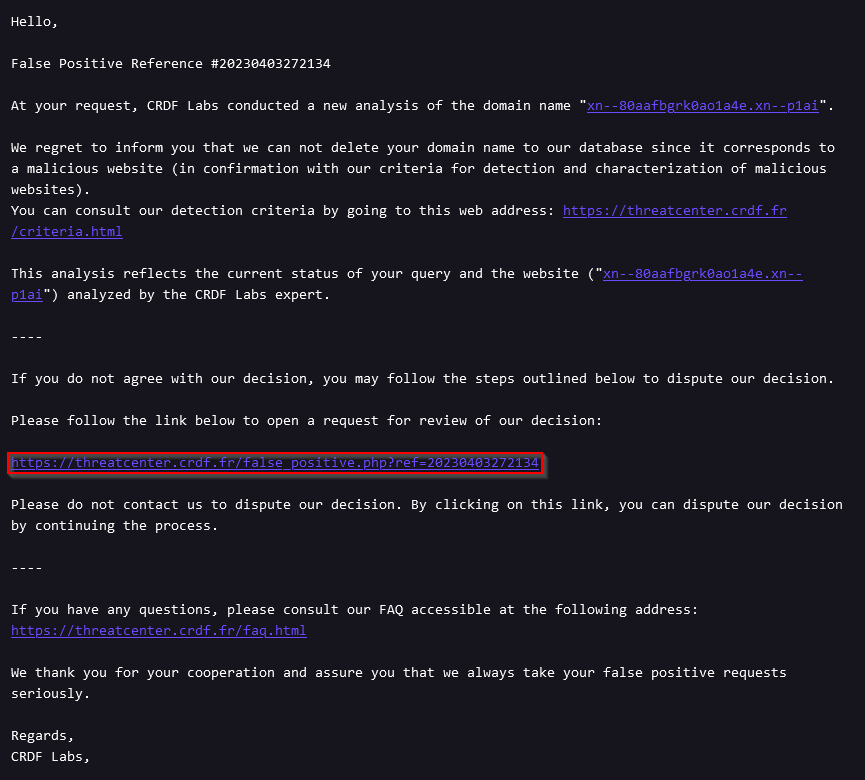
If you do not agree with our decision not to remove your Website from our database Please follow the link included in the email as below.
This link will allow you to explain to us why we should reconsider our decision.
If your website is false positive:
You will receive an email informing you that your domain name has been deleted.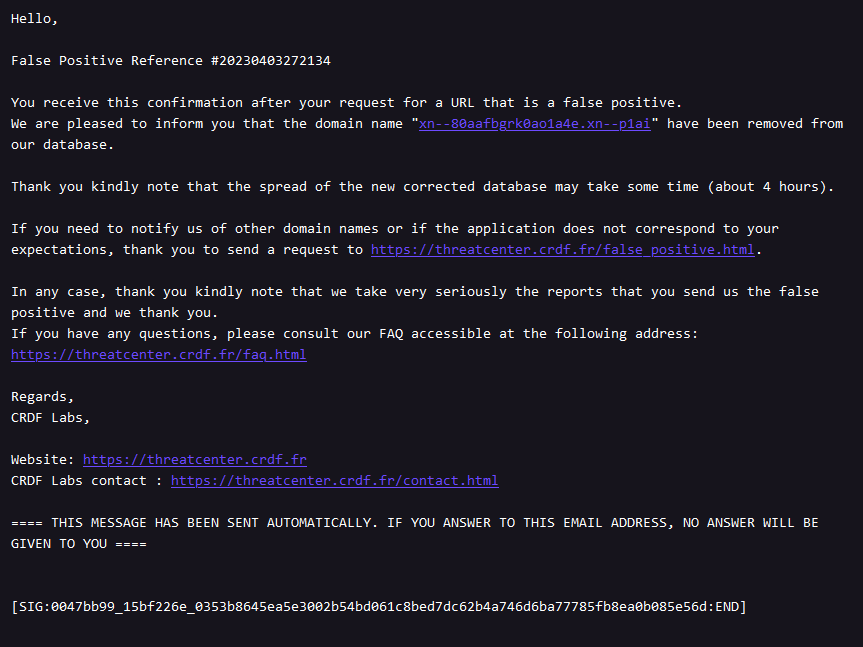
End of the procedure.
Our unique machine learning technology enables us to anticipate future threats and detect current ones. This machine learning system constantly analyzes domain names to find and anticipate future threats. As a result, this engine is able to anticipate threats 7 days before a tag becomes malicious.
This engine detects behaviors and characteristics corresponding to malicious behavior, so that it can be detected with a high degree of anticipation or not.
The development of this engine has enabled us to achieve a 98% success rate, with a false positive rate. We are constantly improving it.
As an input, the system takes a domain name and as an output it tells you the verdict (safe or malicious) and a certainty score.
All data from this engine can be downloaded daily or globally via the private area.
You can also query the API provided for a particular domain name.
Unfortunately, we don't respond to these requests. We understand that it is frustrating not to communicate the reasons for a detection to you with the aim of improving you. However, you need to understand that CRDF Labs' focus is solely on its detection capabilities.
Our business is all about detection, not remediation. Specialists in remediation will be able to advise you and disinfect your website.
CRDF Labs never communicates the elements for which a website has been detected. An attacker could figure out how to bypass our detection methods.
When you submit a Website for a false positive, CRDF Labs performs a thorough, manual analysis. If your Website is still detected as contrary to our detection criteria, we will unfortunately not be able to tell you why it was detected. We recommend that you consult our detection criteria to understand why your Website was detected.
CRDF Labs receives dozens of false positive reports every day and it is impossible to respond personally to all of them. Our responses are mostly automatic to save us time in our false positive management process. We try to improve our process every day to make it simple and effective.
Key points to remember:
- CRDF Labs does not block anything. We cannot impact your business;
- CRDF Labs will not be able to tell you exactly what criteria have been detected on your website;
- The aim of CRDF Labs is to detect websites that present a risk to the user and generate the corresponding CTI (Cyber Threat Intelligence);
- The objective of CRDF Labs is not to provide remediation solutions;
- The objective of CRDF Labs is to process your requests as quickly and efficiently as possible;
- CRDF Labs cannot respond personally to your request. CRDF Labs cannot personally respond to your request. A personal response may be provided if you are unsure about a request or require further information;
- CRDF Labs carries out a manual review of your requests/requests. Only the text is automated. A human actor deals with your requests at all times.
In the process of accessing CRDF Threat Center private data, you must sign the CRDF Labs NDA to continue the registration process on our services.
In case of data exchange, the NDA (Free+Exchange offer) can be mutual according to your needs, and we are able to sign your NDA.
In the case of commercial offers, CRDF Labs does not recognize the conditions of others; only the conditions of CRDF Labs, which will provide you with data, prevail. CRDF Labs will not be able to sign your NDA or a mutual NDA (mNDA).
If you are unable to sign our NDA, CRDF Labs will not be able to continue the validation process.
CRDF Labs never deviates from its validation procedure.